Swiss Data Center
Your data is exclusively yours. As a partner of Infomaniak Network SA, DIGITALABS guarantees your data’s preservation with proprietary online tools that prioritize your privacy and security. Confidentiality is a cornerstone of freedom, and Infomaniak upholds this principle firmly.
Located in Switzerland, Infomaniak SA places your data outside the jurisdiction of the United States and China.
Your data is protected by the Federal Act on Data Protection (nFADP). In addition, Infomaniak complies with the strict rules of the General Data Protection Regulation (GDPR) and serves a large number of European customers.
Selecting your Hosting Service Provider
- How will my data and privacy be protected?
- Where will my data be stored?
- How will my information be processed?
- Who will have access to my personal data?
Infomaniak ensures complete control over its services:
- A longstanding commitment to data protection.
- A business model focused on safeguarding your data, not selling it.
- Data encryption with replication on Infomaniak servers.
- Confidentiality protected by Swiss law and GDPR/LPD compliance.
- Technological independence, with all processes developed in-house, eliminating intermediary suppliers.
Context Analysis
DIGITALABS provides expert advice on Information System Security (ISS), Web Platform Security (back-end, front-end, database and IoT) and provides employees user awareness on online threats.
We conduct on-site assessments for private and SMEs, analyze their operational environment, and deliver customized, high-impact security solutions that enhance (“harden”) web platforms and IT infrastructures.
With 35% of all websites powered by WordPress and over 56 million downloads in 2025, popular CMS platforms remain leading targets for cyberattacks. While standard technologies are widely adopted, they require continuous security enhancements and maintenance to contain evolving threats.
CMS platforms infected in 2024

Vulnerabilities by Type

Identifying Potential Vulnerabilities
The context of an IT project has a significant effect on security. When web applications are the core business of an organisation, there are a number of critical issues that must be followed with standard security protocols. These include:
✅ Modular source code to ensure maintenance and security.
✅ Database integrity by strengthening primary keys, relational links and data encryption.
In web portals, vulnerabilities often appear at external access points, such as:
🔹 Contact forms
🔹 Login and registration forms
🔹 Password recovery systems
🔹 Customer areas (portals) that provide access to sensitive data.
These forms are often the target of attacks when application security is inadequate. Unsecured URLs may also expose sensitive information, making it easier for hackers to extract user IDs or documents.
While high-quality source code is essential, incorporating good practices from the beginning of a website or web application’s creation can effectively prevent intrusions.
Authentication Methods: SFA vs 2FA
The stronger the security, the greater the constraints—for both users and developers. While security is essential, not everyone wants to deal with complex authentication for routine tasks. We need to establish what we want to protect as a priority.
🔑 Single-Factor Authentication (SFA)
SFA relies on one credential (username & password) to verify identity. Despite strong password policies, this method remains vulnerable to:
⚠️ Phishing attacks
⚠️ Credential leaks
⚠️ Human errors
Why 2FA Matters Today?
To truly verify WHO is performing an online action, smartphones serve as the best identifier due to:
✅ Personal ownership – Users rarely lose or lend their phone.
✅ Built-in biometric security – Face ID, Fingerprint, etc.
✅ Stronger authentication – Reduces password dependency.
Finding the Right Balance: The challenge is to enhance security while keeping authentication cost-effective and user-friendly.
Identity Layers
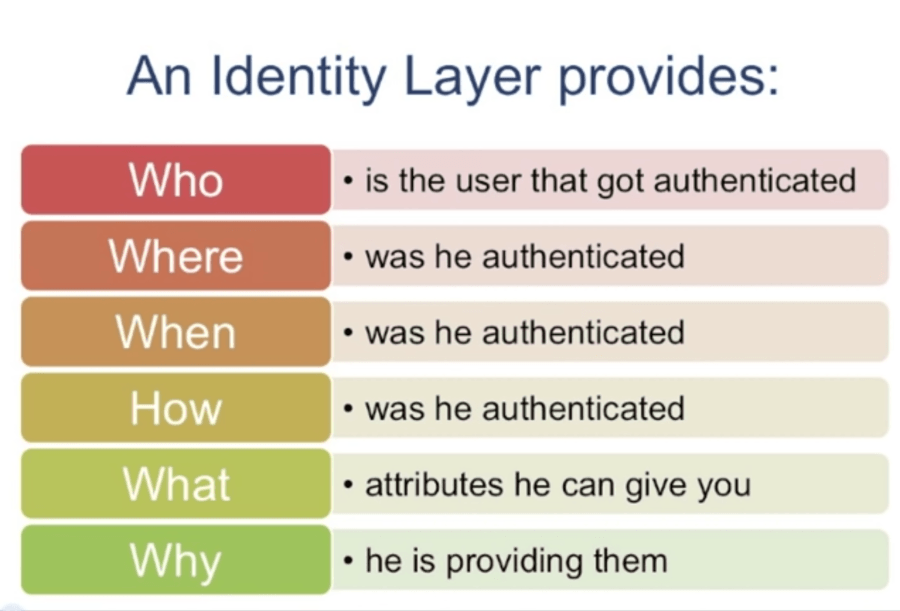
2FA Authentication principle
- Something you KNOW
(user name, password, PIN, etc.) - Something you OWN
(phone, OTP, etc.) - Proving you ARE who you say you are
(biometrics, fingerprint, retina scans, voice recognition, etc.)