Swiss Data Centres - Privacy Meets Security
Your data remains exclusively yours.
As a partner of Infomaniak Network SA, DIGITALABS guarantees the preservation and protection of your information using proprietary solutions that prioritise privacy, integrity and security.
Confidentiality is a cornerstone of freedom, and Infomaniak upholds this principle with firm commitment.
Located entirely in Switzerland, Infomaniak places your data outside the jurisdiction of the United States and China, ensuring maximum sovereignty and neutrality.
Your data is protected under the New Federal Act on Data Protection (nFADP) and complies fully with the General Data Protection Regulation (GDPR), serving a broad European clientele.
Context Analysis - ISS
DIGITALABS provides expert consulting in Information System Security (ISS) and Web Platform Security, covering back-end, front-end, databases, and IoT ecosystems.
We also train employees to raise cyber awareness and reduce exposure to online threats.
Our specialists conduct on-site security assessments for private clients and SMEs, analysing their operational environment to deliver customised, high-impact solutions that strengthen (“harden”) both web platforms and IT infrastructures.
With over 35% of all websites powered by WordPress and more than 56 million downloads in 2025, popular CMS platforms remain prime targets for cyberattacks.
While open-source technologies offer flexibility, they also require continuous updates and proactive maintenance to counter evolving threats.
Vulnerabilities Threats (WordPress)

Data from Wordfence Threat Intelligence provides real-time insight into global cyberattacks, including exploits, brute-force attempts, malware sightings, and top blocked vulnerabilities – highlighting the importance of active protection and monitoring.
Identifying Potential Vulnerabilities
The context of an IT project strongly influences its security posture.
When web applications form the core of a business, strict and standardised security protocols must be followed, including:
✅ Modular and maintainable source code.
✅ Database integrity and encryption.
External access points in web portals:
🔹 Contact forms
🔹 Login or registration interfaces
🔹 Password recovery systems
🔹 External access to sensitive data accessible
Forms are frequent attack targets:
Unsecured URLs may also expose critical information, allowing attackers to retrieve user identifiers or confidential documents.
While high-quality source code is essential, integrating good security practices from the earliest stages of development remains the most effective method to prevent intrusions.
Authentication Methods: SFA vs 2FA
The stronger the security, the greater the constraints—for both users and developers.
Although robust authentication is essential, not every routine action requires complex access control.
Security strategies must focus on what truly needs protection.
🔑 Single-Factor Authentication (SFA)
Relies on a single credential—username and password—to verify identity.
Despite strong password policies, this method remains vulnerable to:
⚠️ Phishing attacks
⚠️ Credential leaks
⚠️ Human errors
Why 2FA Matters Today
To reliably verify who performs an online action, smartphones now serve as the most secure identifier, providing:
✅ Personal ownership – users rarely lose or lend their phone.
✅ Built-in biometric security – Face ID, fingerprint, etc.
✅ Enhanced authentication – reducing dependence on passwords.
The goal is to strengthen security while keeping authentication accessible, cost-effective, and user-friendly.
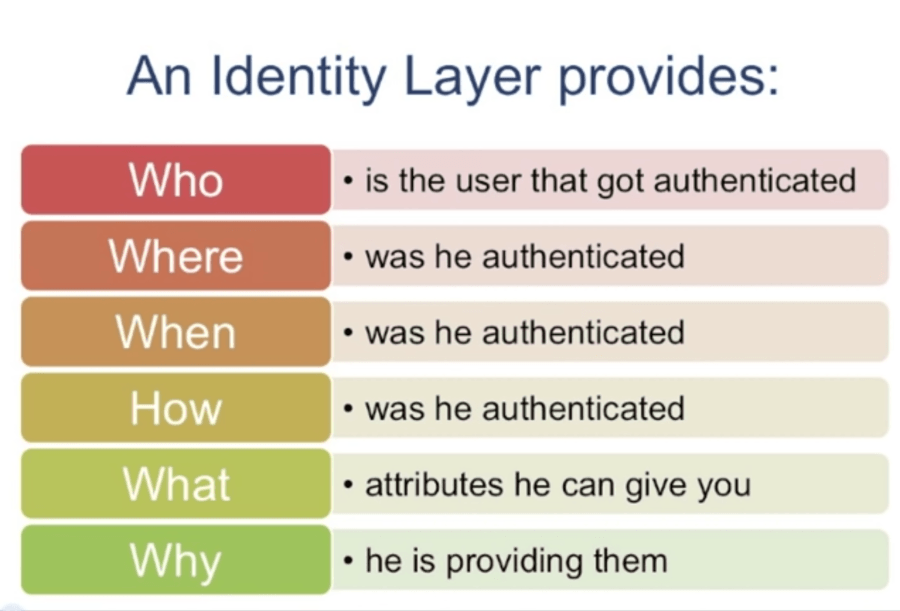
Identity Layers
2FA Authentication Principles
Something you KNOW
(e.g. username, password, PIN)
Something you OWN
(e.g. smartphone, OTP device)
Something you ARE
(e.g. biometric factor — fingerprint, retina scan, voice recognition)
Combining these layers ensures a multi-factor defence against unauthorised access and data breaches.
Cybersecurity is an ongoing process, not a one-time task.
By combining secure infrastructure, strong encryption, reliable authentication, and proactive monitoring, DIGITALABS helps organisations build resilient, compliant, and trustworthy digital ecosystems – ready for tomorrow’s challenges.